The Comprehensive Guide to Public Key Infrastructure (PKI) and Its Crucial Role in Digital Security
The Comprehensive Guide to Public Key Infrastructure (PKI) and Its Crucial Role in Digital Security
In the digital world, where data and communication are at the forefront of every activity, securing it becomes more significant than ever. Whether an online transaction, access to your bank account, or a private e-mail, you need to be certain that your digital interactions are safe from wandering eyes. PKI plays the most significant role in this context by ensuring trustworthy security. It is the basis for most of the encryption as well as authentication that is done in the modern internet-enabled context.
PKI ensures secure communication and verifies identities as well, enabling encrypted transactions to be conducted via multiple digital media. It is derived from a highly advanced system of public and private key pair and digital certificates. Other components of the blog talk about some basic concepts, applications, the types of PKI systems in place, and the difference between a digital signature, electronic signature, and DSC.
What is Public Key Infrastructure (PKI)?
Public Key Infrastructure (PKI) is the set of technologies, processes, and policies that manage digital certificates and public-private key pairs. In other words, PKI allows organizations to secure any communication channel, authenticate who accesses it, and ensure the integrity of the data that passes through it. It does this by binding a public key to an entity such as a person or an organization, ensuring that any communications sent through the internet will be encrypted and that the identity of the sender will be verified.
PKI, in an otherwise trusting digital world where communications often rest on untrusted networks such as the internet, will ensure information exchange over such networks can be safely done and must be used only when authorized parties can decrypt sensitive information. PKI lays the groundwork of a secure connection and is generally implemented in some technology such as Secure Sockets Layer (SSL) and Transport Layer Security (TLS), which, in short, just keeps a website secure.
How PKI Works
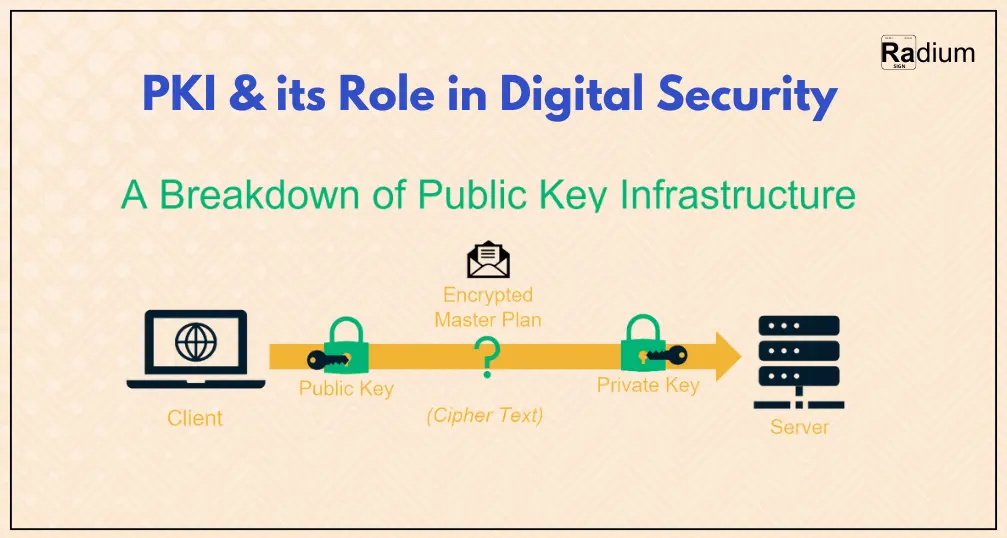
The mechanics of PKI are based on the principle of asymmetric encryption. In the method of asymmetric encryption, each user creates a pair of cryptographic keys; one is public, and the other is private. As each of the keys mathematically connects to the other, it is practically impossible to extract one from the other. The public key can be distributed freely, whereas the private key remains secret.
The sender encrypts the message or data using the recipient's public key. The message can be decrypted only by the recipient who holds the private key. Even if a hacker intercepts the message, he will not be able to decrypt it without the private key.
Digital certificates are a part of the PKI architecture and are linked with a public key with its owner. The digital certificate is issued by a trusted source known as CA. The digital certificate can be regarded as some sort of verification of identity in the digital world, much like a passport or an ID card. This associates a public key with an identity and provides additional information, which can include a name, e-mail, or organization for that identity.
PKI is applied not only for encrypting the message but also authenticating user or device identity. This role of CA makes the task quite important as it validates who is making a request for certificate and, in turn, issuing and attesting for the correctness of the issued certificate.
Where PKI is used
PKI is used in all applications ranging from securing the ordinary communication of people to safeguarding sensitive business information. Among the most popular applications of PKI include:
- Securing Web Traffic: PKI is the essence of securing the web through the use of encryption by SSL/TLS. By clicking on https in the url, you make use of a website's public key to allow for secure interaction between your web browser and their server, that no one has access to.
- Email Security: PKI is used for encryption and signing of e-mail communications. It means that no one but the recipient will be able to read the contents of an e-mail and guarantees that an e-mail originated from a specific sender.
- E-commerce and Financial Transactions: PKI is used on e-commerce sites for securing online transactions. Credit-card holders' information and personal details are kept safe while being sent over the internet.
- Internet of Things: PKI is used for the secure communication of IoT devices. The data for networks across the entities involved, which prevent unauthorized access, is ensured for integrity.
- Enterprise Network Security: Most organizations implement PKI inside their internal network to secure VPNs, wireless networks, and sensitive communications.
Type of PKI system
There are two major forms in which PKI can be implemented: publicly hosted PKI and privately hosted PKI. However, each of these has strength and is preferred based upon the requirements and the infrastructure of an organization.
- Publicly Hosted PKI
Publicly hosted PKI systems rely on third-party Certificate Authorities for management. It means the global-recognized trustworthy third parties could be DigiCert, Sectigo, GlobalSign, among others. A great deal of authentication for public websites happens over publicly hosted PKI systems that assure visitors trust the identity with which they're interacting.
For instance, when you visit an online store and make a purchase, the website uses a publicly issued SSL/TLS certificate that enables it to encrypt transaction information. The CA issues the certificate for the website, verifies its identity, and provides a chain of trust for users.
Public PKI is cheap and efficient as it doesn't force the organization to maintain a CA infrastructure. Moreover, it is globally trusted, which is an important factor when an organization operates in various different countries.
- Privately Hosted PKI
Privately hosted PKI, the name itself depicts that it is fully implemented and managed in the organization's network. It generates, distributes, and maintains certificates in-house without the necessity of having an external CA. Organizations use this internally for security in communication, such as VPN access and email encryption within a company.
In organizations, the private PKI is in full control of issuing certificates and policies. It is predominantly used in huge enterprises or even government agencies for the sake of enhanced security as well as personalization. The privately hosted PKI is actually quite secure. However, to maintain it is quite a costly affair because all things, ranging from the root certificate to the certificate revocation lists, must be handled by the organization itself.
Public vs. Private Certificates
Both public and private certificates are significant for digital security. However, their purposes are different.
- Public certificates: This is issued by a trusted CA for public domains; to be used in the process to secure a website or any form of public service via e-mail. Devices and browsers from around the globe will accept this because of trust from the widely recognized CA issuing them.
- Private certificates: are those issues by the internal CA of an organization and are used for internal purposes. They provide more security to the internal network and communications but are not automatically trusted by the external devices. Therefore, they are required to be configured manually when used out of the secure environment of the organization.
Types of PKI Certificates
PKI certificates have several types. These types differ according to the specific purpose a certificate may satisfy for an end user or organisation. Some of the most implemented types of PKI certificates include:
- SSL/TLS Certificates: SSL/TLS certificates are used for encrypting communications between web browsers and websites. These certificates will ensure that the data exchanged between a user's browser and a server is encrypted and protected against man-in-the-middle attacks.
- Code signing certificates: are used by developers of software. This is through the digital signature of applications where signing an application provides assurance that the software is not tampered with and therefore is coming from a trusted origin.
- Document Signing Certificates: act as a form of cryptographic proof that it is tamper free after signing and is indeed authentic. Most legal agreements and business contracts find their usage.
- S/MIME Certificates: These certificates are used with the intention of message authentication and encryption. They enable the authenticity and confidentiality of emailers' message towards the recipient and ensure receiver confidentiality as well.
Understanding Digital Signatures, Electronic Signatures, and Digital Signature Certificates (DSC)
PKI plays a very significant role in authenticating documents by using digital signatures, electronic signatures, and Digital Signature Certificates (DSC).
What is a Digital Signature Certificate (DSC)?
A Digital Signature Certificate is a type of cryptographic mechanism that binds the identity of a person along with a public key, enabling that person to sign digitally. A CA issues a certificate that has details like user name, email, and a public key which can be used to verify the signature. DSCs provide a high level of security because encryption is needed for verification.
What is an Electronic Signature (E-sign)?
An e-signature is the digital equivalent of a traditional, wet signature. In this regard, however, it is not associated with encryption. As such, it has a potential for other, less consequential forms of transaction, such as authentication by way of email confirmation, PIN code, or one-time passwords.
Key Differences Between DSC and E-sign
Both DSC and e-signatures deal with the completion of the signing process of a document, but their security levels vary. DSC is relatively more secure than e-signatures because it employs encryption and PKI verification. DSCs have the effect of law in many jurisdictions and are applied for high-security purposes like governmental filings, tax submissions, and contracts.
E-signatures are, however more accessible and more appropriate for less critical transactions such as signing simple agreements or online approvals. They typically rely on simple authentication mechanisms that make them easier to use but less secure than DSC.
Common Applications of DSC and E-sign
Both DSCs and e-signatures are widely used in various industries such as:
- Online Banking: Digitally sign the transaction.
- E-commerce: For customer identity verification when shopping online.
- Business contracts: For making a legal binding contract.
- Government Submissions: Required for income tax returns, regulatory filings, and official documents.
- HR Departments: Where employee contract and payroll form is signed.
Benefits of PKI in Digital Security
PKI, indeed, falls under the larger umbrella of a modern digital security landscape. However, it serves many benefits:
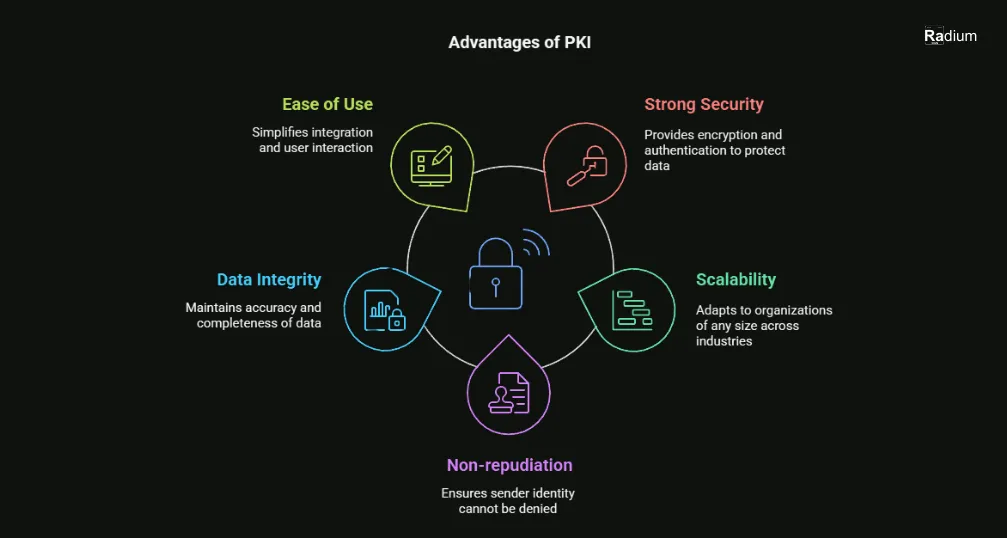
- Data Encryption: PKI provides confidential information like credit card numbers, personal details etc. encrypted in order to stay safe from any cyber attack.
- Authentication: PKI authenticates the identities of users, devices, and systems, thereby providing assurance that only authorized parties are allowed to access critical resources.
- Integrity: PKI safeguards the integrity of data and transactions by ensuring information has not been altered during its transmission.
- Non-repudiation: Using PKI, users are unable to repudiate any signed document or participation in any transaction, creating a legal as well as an audit trail.
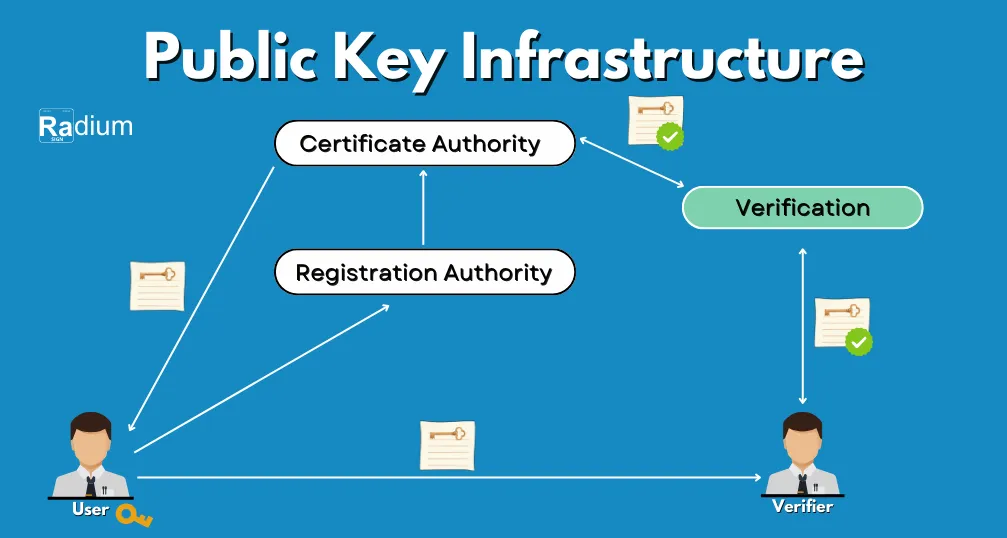
PKI Components at a Glance
PKI is made up of several basic elements:
- Public and Private keys: Pairs to be used for encrypting and decrypting.
- Digital certificates: Public-key certificates that correlate identities with public keys.
- Certificate Authorities (CA): Organization that issues the certificates and verify them.
- Registration Authorities: These are the ones that check on any certificate request made before it is issued.
- Certificate Databases: Respositories for keeping and managing the certificates.
Conclusion
PKI is a cornerstone in securing the digital communication and transactions and for identity verification. Whether used in website encryption, secure emails, or protection within an internal network, PKI provides a powerful framework to achieve confidentiality, integrity, and trust across digital domains. This would require an understanding of its constituent parts, uses, and the differences between a digital signature, electronic signature, and DSCs while traversing the changing digital landscape in a safe and secure manner. PKI enables the organizations to further increase their level of security and make the internet a much more trustworthy domain for their users.