Root Certificates in India: The Backbone of Digital Trust
Root Certificates in India: The Backbone of Digital Trust

In the fast-changing digital world of India, providing secure and reliable online experiences is the need of the hour. Root Certificates come first here, plain vanilla building blocks which enable trust to exist on networks and the internet. This detailed study goes into the nuts and bolts of root certificates, how they are relevant in the Indian digital ecosystem, the role the Root Certifying Authority of India (RCAI) plays, the issues and best practices associated with using them.
Understanding Root Certificates
A Root Certificate is an electronically issued certificate from a trusted entity called a Certificate Authority (CA). This root certificate forms the foundation of a hierarchical construct named the Public Key Infrastructure (PKI) which verifies and ensures communications among devices, programs, and sites. The authority of the root certificate is passed via a chain of trust consisting of intermediate certificates right down to the end-user certificates. This infrastructure guarantees entities who participate in electronic communications to be authenticated and reputable.
The Public Key Infrastructure (PKI) Hierarchy
PKI hierarchy is a multi-level system that establishes and maintains a secure environment for digital messages. Root Certificate Authority (Root CA) is the top of the hierarchy, which has a self-signed root certificate. Root CA validates lower or intermediate CAs by digital signatures on their certificates. Intermediate CAs sign certificates to end entities such as individuals, organizations, or devices. The security and authenticity of the root certificate validate the integrity of the entire system.
Chain of Trust
The PKI model is based upon the concept of a chain of trust. This is the process of sequential validation of certificates from the root certificate down to the end-entity certificate. If a user attempts to make a secure connection to a website, the server shows its digital certificate. The user's system would then backtrack this certificate via the chain of trust to a trusted root certificate it has stored in its certificate store. If there is a break or an untrusted link in this chain that exists, the connection would be declared insecure, and the user is warned of risks.
The Role of the Root Certifying Authority of India (RCAI)
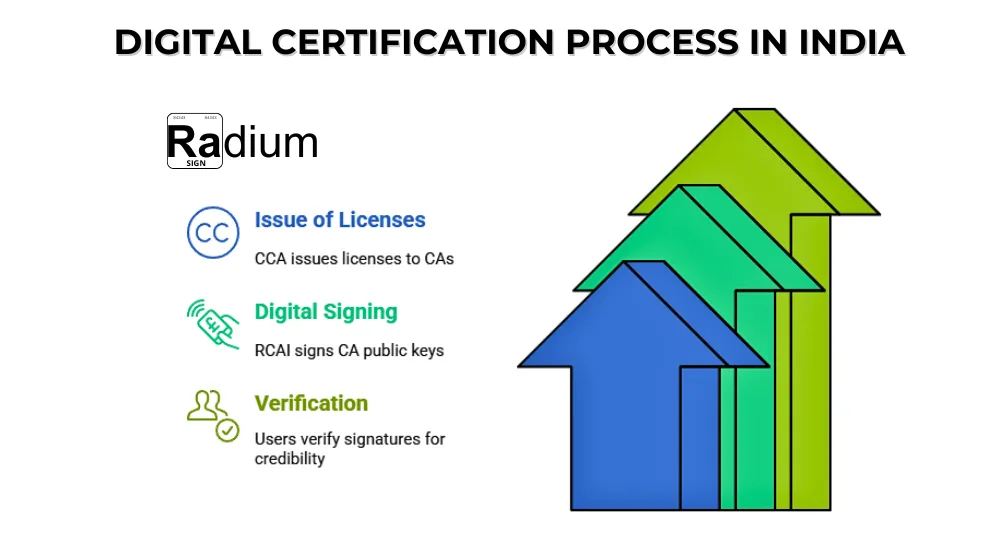
In India, the authenticity of electronic certifications is guaranteed by the Root Certifying Authority of India (RCAI), established under Section 18(b) of the Information Technology Act, 2000. Controlled by the Controller of Certifying Authorities (CCA), the RCAI electronically signs the public keys of the licensed Certifying Authorities (CAs) in the nation. The process involves:
-
Issue of Licenses: The CCA issues licenses to CAs that allow them to issue digital certificates to the end-users.
-
Digital Signing: The RCAI digitally signs the public keys corresponding to the private signing keys of such licensed CAs, establishing a trusted root for all the certificates issued under its hierarchy.
-
Verification: Reliance parties can check these signatures through the site of the official CCA or the website of the respective CA, thereby creating digital certificates credible.
Establishment and Functioning of RCAI
The RCAI was established to promote the growth of e-commerce and e-governance in India by providing a robust infrastructure for digital signatures. By verifying the public keys of trusted CAs, the RCAI ensures that individuals within cyberspace can establish that a particular certificate has been issued by a valid and trusted CA. It is this infrastructure of trust that is most essential to electronic communications and transactional security.
Licensing of Certifying Authorities
The licensing process for CAs in India is strict, and it ensures that only those organizations satisfying certain conditions are licensed to provide digital certificates. The applicants are required to show financial stability, technical competence, and compliance with security measures. The CCA assesses all these aspects prior to issuing the licenses, thus ensuring the validity of the digital certification process.
Significance of Root Certificates to India's Cyber Space
Root certificates are the backbone of India's fast-growing virtual platform for a variety of reasons:
-
Secure Online Transactions: As e-commerce, online banking, and services grew, root certificates rendered all online transactions between consumers and service providers safe and encrypted, protecting sensitive information from cyber attacks.
-
Authentication of Government Services: As the Indian government goes all out more in making a push to become digital, tenders such as the Digital India initiative, root certificates authenticate government websites and services, ensuring citizens that they are legitimate and safe.
-
Facilitation of Digital Signatures: Root certificates facilitate digital signatures, which may be conferred legal status under the Information Technology Act, 2000. It facilitates paperless transactions, e-governance, and business process automation.
-
Creating User Trust: A trusted origin with an indication that traces to a legitimate digital certificate creates user trust in sites' and online service's security and authenticity.
Challenges and Considerations
Although their critical role, the use and administration of root certificates in India are subjected to some challenges:
Trust and Recognition
There have been instances where the RCAI certificates were not being recognized by global platforms, which caused security warnings to users. In 2018, for example, users were cautioned against the installation of unauthorized root certificates since it would lead to potential security risks. citeturn0search1
This lack of recognition is due to differences in validation processes and security needs between the RCAI and the global community. To combat this, there is a need for increased cooperation and harmonization of standards for mutual recognition of certificates.
User Awareness
The majority of users would have no idea what the security warning on certificates implied and might in their ignorance threaten their own security by ignoring or introducing foreign certificates. This reveals a requirement for intensive user training in the relevance of digital certificates and the concomitant consequences of untrusted sources.
Technological Advancements
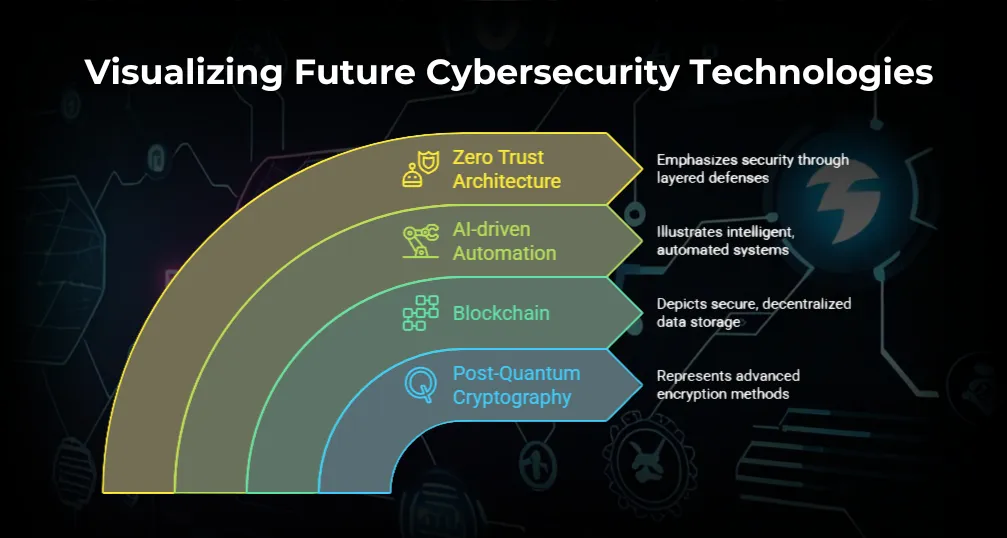
The pace of technology advancement requires that cryptographic standards and security measures be constantly updated. As cyber threats continue to become more sophisticated, older encryption techniques can become useless, and thus research and evolving to new technologies must be continuous.
-
Post-Quantum Cryptography (PQC) – With the progress of quantum computing, current cryptographic techniques such as RSA and ECC will be at risk. India needs to be ready for a post-quantum world by embracing quantum-resistant cryptographic algorithms to protect root certificates. The National Informatics Centre (NIC) and central government agencies need to explore and implement PQC standards ahead of time.
-
Blockchain-Based Digital Certificates – Blockchain technology provides a decentralized and tamper-proof method of issuing and authenticating digital certificates. India's use of blockchain for land records, academic qualifications, and digital identity authentication (e.g., through Aadhaar) can be applied to root certificate authentication, mitigating the threats of certificate forgery and MITM (Man-in-the-Middle) attacks.
-
Automation of Certificate Lifecycle Management – Firms and institutions are increasingly using automated certificate management software to scan, renew, and revoke certificates efficiently. Use of AI-driven monitoring software can avoid possible security breaches due to expired or faulty certificates.
-
Zero Trust Architecture (ZTA) – As more sophisticated cyber attacks emerge, India needs to deploy a Zero Trust security model depending on ongoing confirmation instead of innate trust. Root certificates are very crucial in ZTA because they enable secure authentication across networks, devices, and cloud environments.
Best Practices for Strengthening India's Root Certificate Infrastructure
To increase the security and reliability of root certificates in India, the stakeholders need to implement some best practices:
Strengthening Regulatory Frameworks
-
The Controller of Certifying Authorities (CCA) is required from time to time to update guidelines based on international standards for cybersecurity like NIST (National Institute of Standards and Technology) and ISO 27001.
-
Periodic auditing of licensed Certifying Authorities (CAs) will help to ensure compliance and identify vulnerabilities before they are exploited.
Enhancing Public Awareness and Education
-
Campaigns should warn users of the dangers of accepting unverified certificates and request them to verify digital signatures before they make online transactions.
-
Developers and companies must learn how to include secure authentication methods in websites and applications.
International Collaboration
-
India must partner with international cybersecurity bodies and technology giants such as Google, Microsoft, and Mozilla to make Indian root certificates internationally accepted, so Indian users are not provided with security warnings on international platforms.
Strengthening Infrastructure Security
-
having available trusted Hardware Security Modules (HSMs) for root certificate storage can forestall key compromise threats.
-
Regular penetration testing and security audit must be carried out on India's Root Certifying Authority (RCAI) and its infrastructures.
Conclusion
Root certificates are the foundation of India's digital trust and are important for making online transactions, e-governance services, and digital communication secure. With growing use of digital platforms, it is more important than ever that India's certificate infrastructure is fortified. Through the adoption of technological innovation, stricter regulation, and the formation of international partnerships, India can build a strong and internationally accepted root certificate system.
The way to safe and trusted digital India is only achieved through initiatives by government agencies, industry, and citizens in general. Placing digital security at the forefront of the agenda will allow India to head in the correct direction towards its vision of a digitally empowered nation.
Root certificates are the backbone of secure digital communications, especially in a nation going digital at a rapid rate like India. India's Root Certifying Authority is one of the most important contributors to the facilitation and provision of this trust infrastructure. However, both the users and the service providers must be vigilant, ensuring that digital certificates are properly managed, authenticated, and trusted, thereby securing India's digital space.